TL;DR: More applications and tools now support Bring Your Own Identity Provider (BYO IDP), allowing your organisation to establish centralised identity management across various apps and platforms. However, a gap remains in automating and aligning access controls between the IDP and the connected platforms. This gap can lead to manual overheads, inconsistent permission models, and increased security risks. This blog explores approaches to addressing this concern, with a deep dive example integrating Microsoft EntraID with GoodData.
As enterprise ecosystems become more complex and increasingly hybrid, developer teams frequently combine cloud-native tools with third-party platforms. Implementing this in a way that is scalable, secure, and team-friendly is a challenge. Teams struggle with manual processes and redundancies that lead to increased inefficiencies and costs.
For example, at a recent engagement, our client team used a third-party data platform that allowed single sign-on integration with their central cloud ID solution. However, the data platform did not support fine-grained permissions tied directly to enterprise roles. This resulted in two separate user lists, one in the IDP and the other in the third-party application, each with its own independent permission models.
Managing both users and permissions across two disconnected systems created the following risks:
Misconfigured access (e.g., overly broad or missing permissions)
Onboarding delays and manual errors
Inconsistent audit trails and compliance gaps
We implemented an automation workflow that integrated identity management across both systems. Our solution reduced the manual provisioning time by 80% while improving access consistency across identity and analytics platforms.
Measurable business outcomes:
Improved operational efficiency - Automated integration reduced the overhead of managing user access across multiple platforms, resulting in faster onboarding and fewer manual errors.
Strengthened security posture - Automation ensured consistent access control across environments, preventing misconfigurations and missed access updates.
Supported on-going compliance - Version-controlled access configurations enhanced auditability and improved accountability, supporting reporting for compliance.
Supported future growth - Our solution was scalable and reusable across multiple data platforms, including Snowflake and Tableau, allowing the client to grow or integrate with other data platforms in the future as needed.
The Hybrid Identity Challenge
The original manual integration worked as follows.
The Ops team created users in the IDP (in our client’s case, Microsoft Entra ID) and assigned them to enterprise applications.
The Data team then manually recreated users in the third-party app (in our client’s case, the GoodData analytics platform) and configured a platform-specific role.
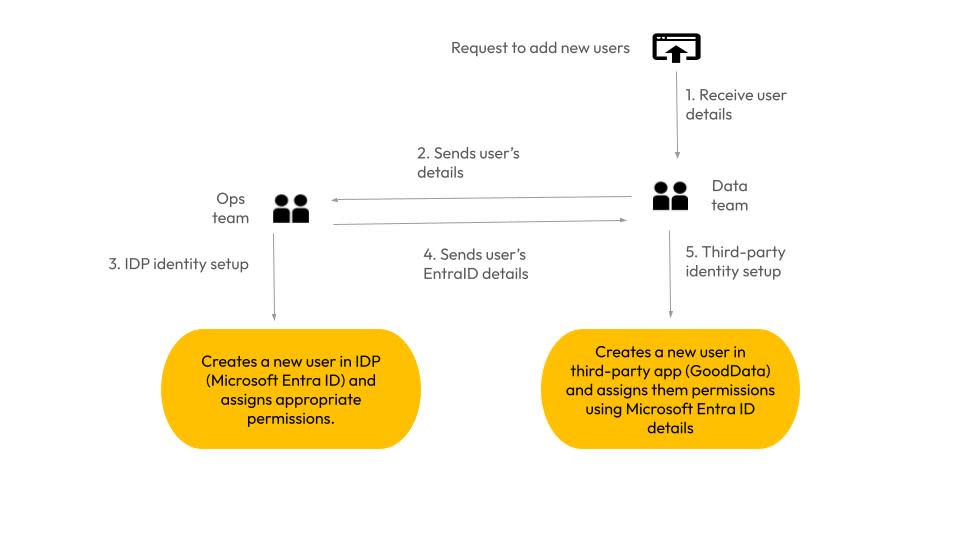
The redundant workflow
The client sought a scalable and maintainable identity integration solution that balanced the needs of both the Ops and the Data team. They wanted a setup where:
The Ops team manages identities and user lifecycles in Microsoft Entra ID.
The Data team controls data access and permissions in GoodData
The solution avoids manual, error-prone synchronisation steps between the two systems.
The V2 AI solution
The core principle of our solution was the separation of responsibilities. By aligning each team to their area of ownership, we created a structure that scales without bottlenecks.
Ops Fully Owns Identity
The Ops team manages user lifecycles in Microsoft Entra ID, including inviting users, assigning them to groups, and managing enterprise app roles. They are not responsible for what happens inside GoodData and do not need platform-specific context.
Data Teams Own Access Logic
The data team defines how users are grouped and permissioned within GoodData. This includes managing workspace roles, group definitions, and row-level filters. They do not (and often should not) have access to Entra ID.
Automation Bridges the Two
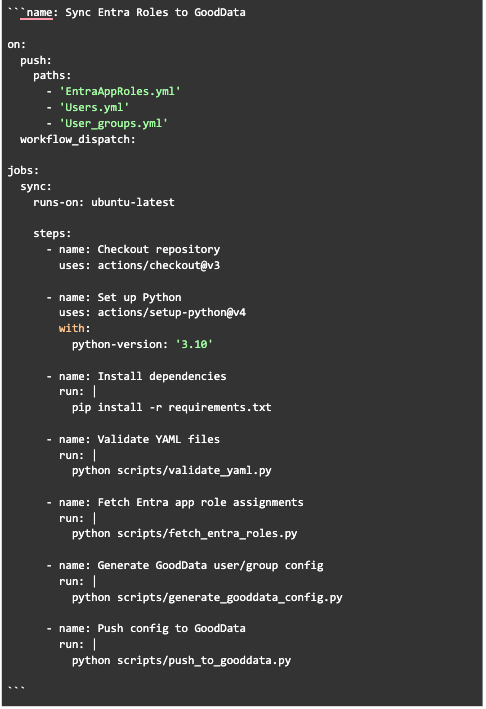
A GitHub workflow (A configurable automated process running one or more jobs) pulls role assignments from Entra ID and applies them to GoodData in a consistent, version-controlled manner. This ensures that both teams can operate independently while staying in sync.
The automation eliminates manual steps, reduces the risk of human error, and guarantees traceability for every change. It also allows each team to use the tools they’re most comfortable with without disrupting each other’s workflows.
The Technical Details
We created a lightweight integration layer between Microsoft Entra ID and GoodData, leveraging:
Microsoft Entra ID Enterprise App Roles
GoodData’s REST API for automating role provisioning
An automation workflow (using GitHub Actions) to link the two
GitHub Actions allows developers to define configurable automated processes that execute a series of jobs in response to events within a GitHub repository.
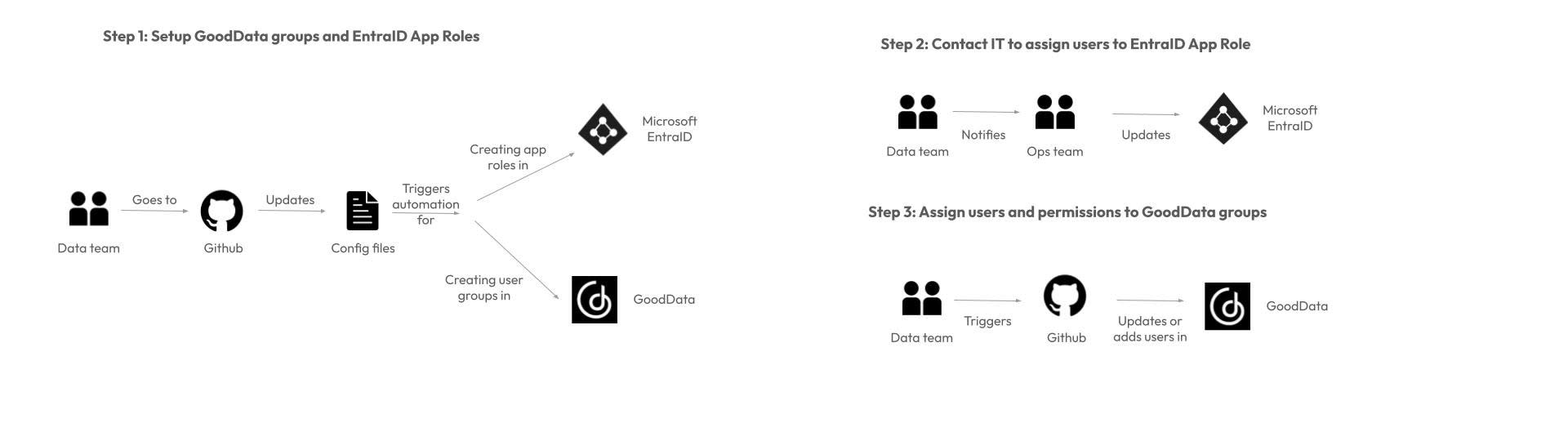
The outcome:
Ops continues to own identity, inviting and assigning users via Entra ID
The data team defines which roles unlock what access in GoodData
Our automation handles the propagation—Just a click of a button.
Step 1: Define Roles and Groups in GitHub
The Data team defines:
Enterprise roles in EntraAppRoles.yml
GoodData group mappings in user_groups.yml
Example methods used for syncing Entra ID app roles:
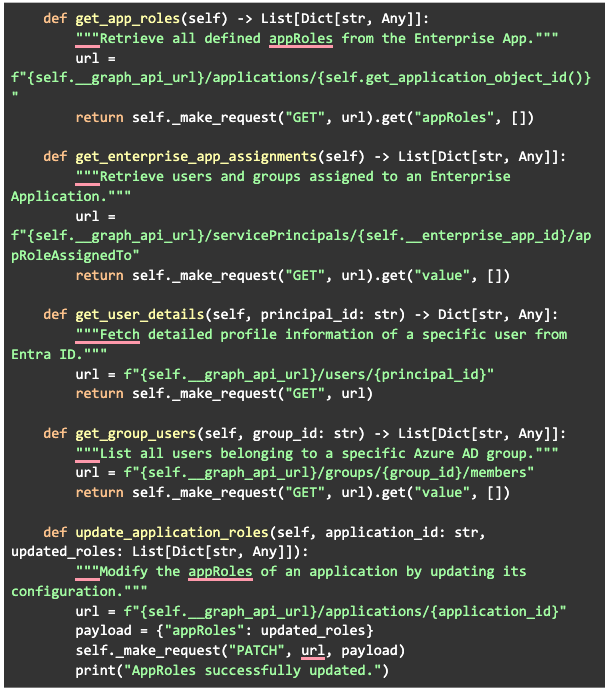
Once committed, this triggers a GitHub Actions workflow that:
Creates/updates App Roles in Entra ID
Creates/updates user groups in GoodData
Step 2: Assign Users in Entra ID
The Ops team assigns users to the appropriate App Roles in Entra ID. This is handled entirely within identity management tools—no need for platform-specific access or coordination. The team should already have been trained for this, so no extra knowledge transfer work is required.
Step 3: Sync Users and Permissions in GoodData
A workflow pulls user-role mappings from Entra ID and:
• Generates the users.yml and user_groups.yml files
• Pushes them to GoodData via API
• Applies workspace access and data filters
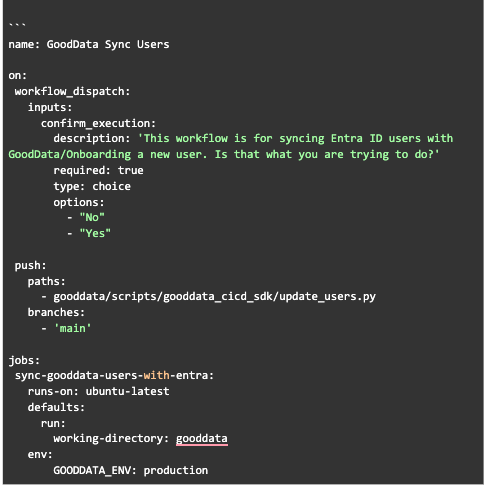
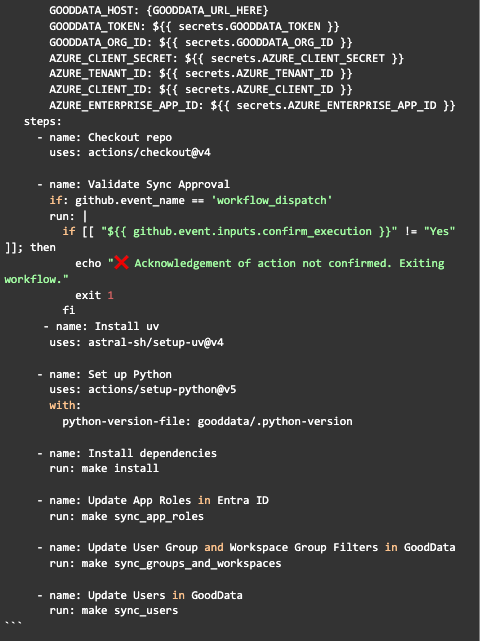
With this setup, the Ops team could simply invite or assign users in Microsoft Entra ID. The Data team had the flexibility to define and manage role-based permissions in GoodData. Our automation workflows propagated role assignments end-to-end, with no need for manual sync.
Final Words
Bringing identity and access together in a hybrid environment empowers organisations to establish clear responsibilities across IT operations and data governance, while maintaining a unified and scalable access control system. Automating the integration between identity providers and analytics platforms reduces manual effort, improves security, and ensures that access decisions are both transparent and auditable. It accelerates onboarding, simplifies role changes, and enables teams to operate independently without unnecessary coordination, which is essential in environments where agility and compliance are equally important.




